Il modulo Hack-Back è spendibile in ambienti Militari/Governativi di alto valore strategico, in quanto è in grado di difendere quelle infrastrutture che necessitano di una protezione informatica attiva.
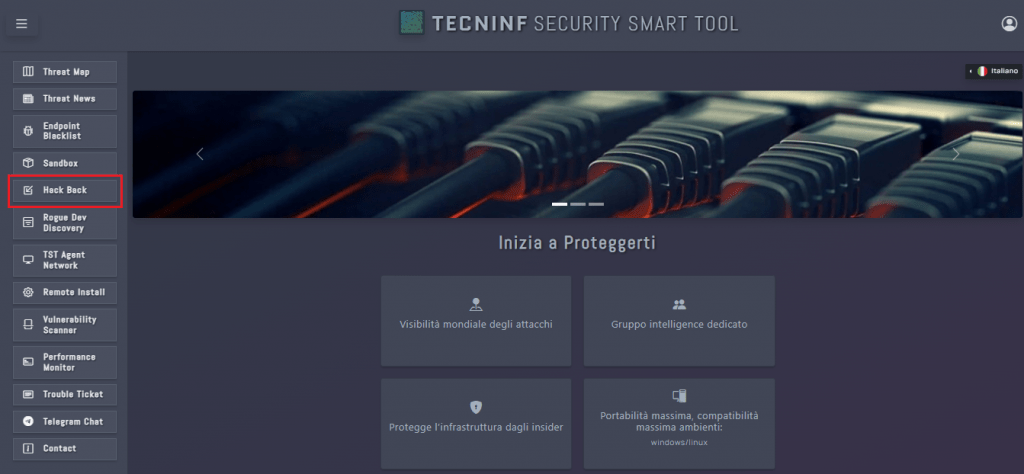
È il modulo core della TssT, permette di difendere l’infrastruttura attivamente contrattaccando i target rilevati come attaccanti
Un attacco al quale può reagire può essere simile a quello ricevuto dai molti siti governativi e istituzioni bancarie ucraine,e cioè una tipologia di attacco denominata DDoS. In questo caso il modulo Hack Back sarebbe stato in grado di dare una risposta efficace.
DDoS è l’acronimo di Distribuited Denial of Service e il significato è quello di interruzione distribuita del servizio.
Con questa tecnica si inonda un sito di richieste in modo che la risposta a queste, simultaneamente, diventa ingestibile dalle risorse disponibili.
Questa situazione mette il sito e le sue risorse fuori uso.
Nella tipologia di attacco DDoS le richieste provengono da una molteplicità di fonti, le quali possono essere dei computer infettati che formano una rete denominata Botnet.
Il modulo Hack-Back è stato sviluppato per intercettare anche questa tipologia di attacchi, contrattaccando e mettendo in atto quattro fasi di attacco con l’obiettivo di difendere l’infrastruttura.
HB
01
Di seguito le fasi messe in atto dal modulo per difendere attivamente:
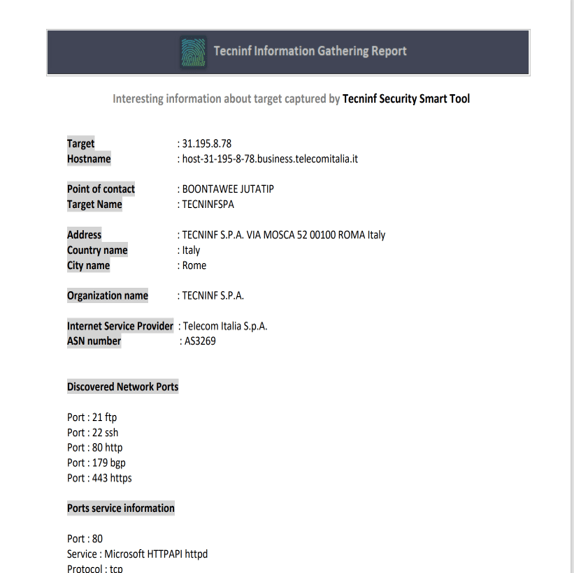
- information Ghatering: rileva informazioni sensibili del target ;
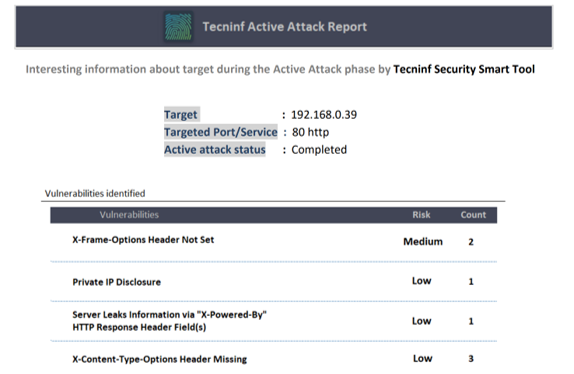
- Active Attack: attacca il target con gli attacchi Cross Site Scripting, Sql Injection e Path Traversal;
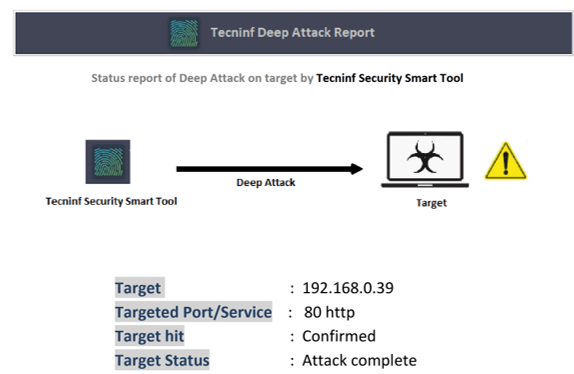
- Deep Attack: attacca il target eseguendo un Ddos;
- Send APT: invia tramite il vettore e-mail un payload Keylogger al target attaccato.
02
Per tutte le fasi verranno erogate varie tipologie di report proprietari che dettagliano le caratteristiche e i risultati rilevati.