The word Botnet comes from roBOT NETwork . As the term already anticipates, it is a network made up of compromised computer devices (therefore infected by Malware ) and connected to the Internet, controlled by a single entity, the botmaster . A botnet can have both benevolent and malicious purposes, and can:
- act on a large computer network remotely;
- automatically analyze the devices and networks connected to them;
- perform attacks DOS ;
- perform spam attacks;
- corrupt other devices.
Creating a Botnet
The attacker needs, first of all, a compromised and infected machine to use as zombie . The Bot is programmed to search for other vulnerable devices, infect them in turn and thus creating a large network of compromised targets.
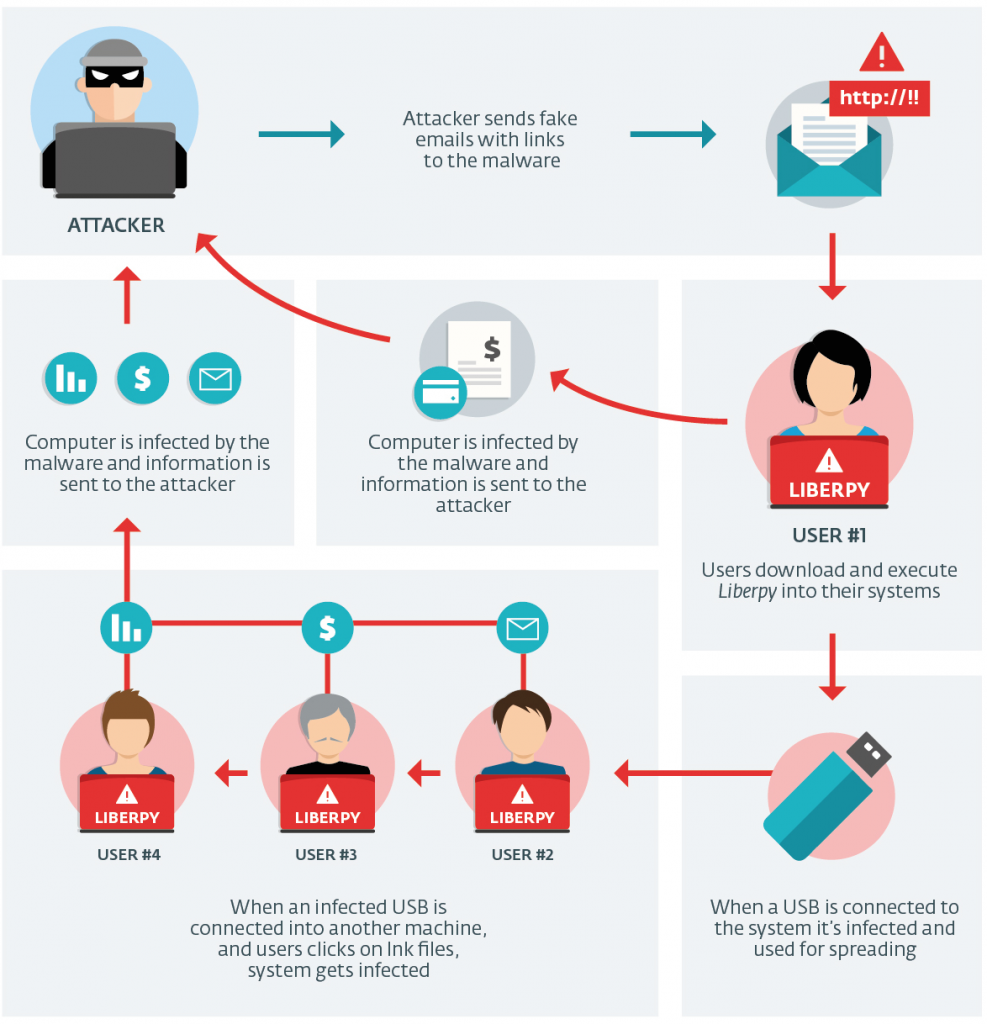
The attacker creates a C&C center ( commands and controls ) by configuring and forcing the various hosts to connect and wait for instructions. Through that center it is now possible to command them simultaneously, launch D attacks DoS (Distributed Denial of Service) or infect other devices.
Main types of botnets:
- Centralized : they are controlled by a single C&C, which issues the commands and controls them in total. However, if the botmaster is tracked down and rendered harmless, they will no longer perform their function;
- Decentralized (via p2p): they are linked together as a network of peers and each gives orders to neighboring nodes. In this way, even if one is stopped, the others continue to do their job anyway.
The simplest way to control a botnet is to connect each bot to a remote server. In this case, a single control source could send commands and updates with synchronous or asynchronous communication methods, which differ as follows:
- Asynchronous: based on HTTP, it foresees a connection to a Web server to load / execute instructions at predefined intervals;
- Synchronous: based on IRC (Internet Relay Chat), it consists in establishing a persistent channel (chat) between the bots and the IRC server to receive commands in real time.
The centrality of these configurations makes them, however, particularly vulnerable. In fact, to annihilate the functionality of the entire botnet it would be enough to simply identify and obscure the C2 server (HTTP / IRC).
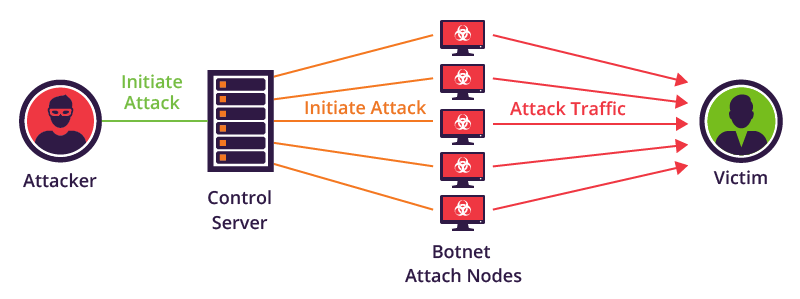
Hackers’ choices
Hackers are therefore faced with several choices:
- The ability to implement a peer-to-peer (P2P) distributed communication mode . In this scenario, where a zombie device can act as both a bot and a C2 server, there is no point of reference from which the bots get their instructions. The latter configuration, although less widespread due to the construction complexity, would be less vulnerable to a possible counterattack. It would be more problematic to obscure all bots to destroy the functionality of the entire botnet;
- The possibility of implementing a mixed communication mode . A good solution could be to adopt a configuration trying to reap all the advantages of centralized / P2P control modes. For example, creating a P2P botnet to communicate with C2 servers via HTTP protocol;
- The possibility of implementing a communication mode using the TOR network . This network, as known, being encrypted and designed to be anonymous would allow to hide botnet actions. End of form
Objective of Botnets:
Allow the simultaneous action of hundreds of thousands of devices that could be used by botmasters for different purposes:
- to perform DDoS attacks (Distributed Denial of Service) on Web servers, targeting a website with anomalous traffic, in order to overload the services by blocking their operation;
- for spamming . In fact, botnets appear to be the main means used for this purpose;
- for web fraud . The simulation of clicks on advertising links or the loading in the background of websites (perhaps unrelated to these activities), could be a source of fraudulent profits, if these sites pay based on the number of clicks or views;
- to mine Bitcoin , using the computing power of zombie computers;
- to distribute other malware . As we have seen, botnet infections spread through malware / Trojans which, by identifying the vulnerabilities of outdated (or outdated) firewall or antivirus systems, download other malicious software (adware, spyware, ransomware etc.) for a wide range of illicit uses and data breach;
- to rent MaaS (https://maas.io/) and / or other paid malicious services.
There are several software for creating these networks. Recalling that use for illegal purposes is punishable by law , some of the best known are:
- Botnet Trojan Shark : it is a software for controlling Windows machines, it bypasses certain firewalls, all traffic sent is encrypted and also has keylogging capabilities;
- Poison Ivy : as above, you can find l ink for download and a practical laboratory at this address.
- PlugBot : is a Hardware Botnet, created for a research project. Official site .
- Illusion Bot ;
- Netbot attacker .
- PBot Malware
A practical example: The PBot DDoS malware, used to launch Akamai’s largest DDoS attacks in Q2 2017. In the case of the PBot malware, malicious users used PHP code that dates back decades to generate a massive DDoS attack. The attackers managed to create a mini DDoS botnet capable of launching a 75 gigabits per second (Gbps) DDoS attack. It is interesting to note that the PBot botnet was made up of a relatively small number of nodes, about 400, yet capable of generating a significant level of attack traffic.
Contrast and international analysis
Botnets are one of the main security risks in recent years, as they are able to give computing power and bandwidth to people with not strictly legal purposes. Detecting them and putting them offline requires a disproportionate amount of time and energy, as finding an infected machine does not necessarily imply being able to trace the botmaster (especially if controlled by TOR , for example).
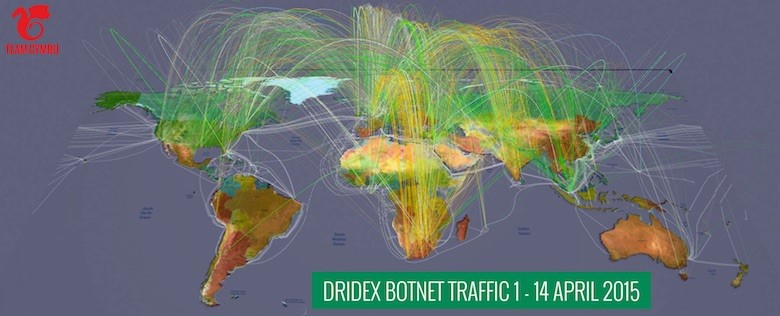
A cybersecurity team was able to largely analyze the Dridex botnet and the traffic it generates (it is still active). This propagates through email attachments ( never open them without first analyzing them ), and is auto-sent to the contacts in the victim’s address book. The analysis, in English, can be found at this address (of particular interest also the video ). Another aspect to consider and analyze consists of the malicious activities detected in the last month around the world, organized in a video that can be downloaded or viewed directly from here.
Recently, the news about the disappearance of the world’s largest Botnet has made headlines. This fact has vanished , simply disappeared without leaving a trace of itself. It was already it was destroyed in October 2015, by a task force of NCA and FBI, but somehow she was resurrected and returned to “work”, spreading the ransomware Locky . More details can be found at securityaffairs and vice .
How to defend against botnets
The defense against this ever-changing threat is to protect the network and potential accesses, i.e. users (who should be properly educated about the threat and its management).
A fundamental role is played by the human factor and by all those aspects related to users’ carelessness in respecting good safety rules.
In fact, an infected email, the download of an uncontrolled program or an exlpoit that exploits security flaws to make a device (PC, mobile device, IoT system) become a zombie is enough. So here are some minimum security tips for users to always keep in mind:
- update your device with the latest versions of the operating system and / or firmware;
- protect your device with up-to-date antivirus and firewall applications;
- download trusted and verified software / app and update it periodically;
- pay attention to attachments and links in e-mail messages.
Defense for companies – How to reduce exposure to botnet risk
Defense certainly passes through the digital education of users, but it is also true that companies themselves can develop some precautions to defend themselves. In particular, some basic precautions are:
- Use tools to stop the flow of unwanted and high-risk emails containing malicious attachments;
- provide tools to filter outgoing content from the corporate network, access and limit exposure to threats, in order to prevent any interactions between an established malware bot and its C2 server;
- counteract any lateral spread of the infection, within the network, by implementing restrictions on the trust relationships of domains and local administrative accounts;
- intensify detection of unusual activity through improved network and connection monitoring;
- offer training and frequent updates to employees on network security support rules on cyber threats and any scams perpetrated through phishing or other techniques.

