The TssT Tecninf Security Smart Tool was created under the growing pressure of the worldwide diffusion of the cyber attack surface, as well as the urgent need to have an Italian product of IT security, completely created and developed by a team of Italian cybersecurity experts.
In addition, the TssT gives maximum capacity for action to CISOs, in their daily activity of repression of cybercrime and to security analysts, by enhancing analysis skills. Furthermore, it supports SOC (Security Operation Centers) in the daily monitoring of the cybersecurity landscape.
TssT
01
TECNINF SECURITY SMART TOOL
TssT is a specialized product to work in complete affinity with SIEM systems, a specialized product to perform SOAR automation functions.
It is composed of a set of vertical cybersecurity features, able to protect an infrastructure no longer passively or reactively, but actively.
02
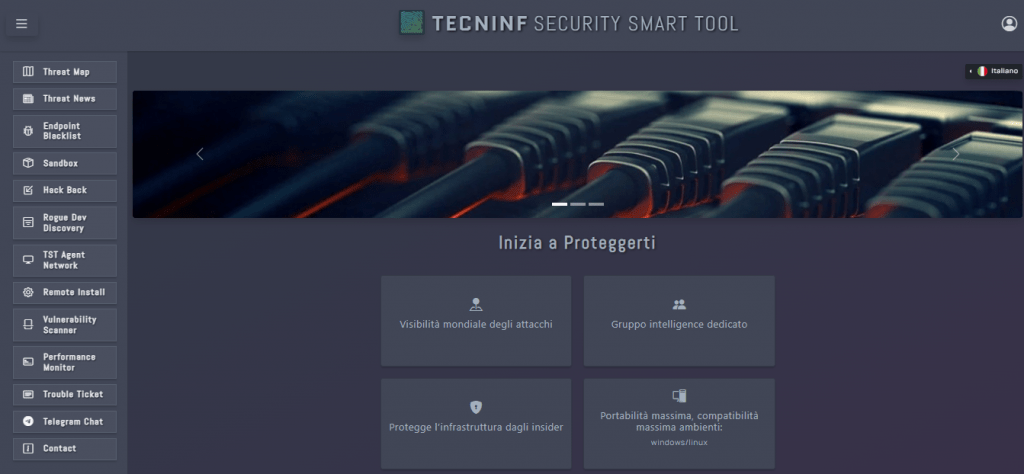
DASHBOARD / AGENT INFRASTRUCTURE
The TssT is based on a Dashboard / Agent infrastructure system.
The software is installed on Debian OS and Docker containers, which perform some vital functions. All this gives the feature of extreme portability to its core engine, even on a Windows based system.
Developed using the Java Spring Boot and React framework, it uses an API layer and a set of open-source and paid sources to intercept global attacks.
03
MODULAR CYBERSECURITY
The TssT is made up of the modules listed below, which all work related to each other in a perpetual and functional cycle.
TN
THREAT NEWS
It is able to detect news about cyber attacks worldwide, reporting the description of the indicators of compromise (IOC).
Furthermore, there is a filter to highlight only the news detected by the TECNINF Intelligence Group (TIG).
In the module there is an option to get Italian news.
News can be sent to a customer list or to the supply chain by email.
The news is collected from paid open source sources.
TM
THREAT MAP
The Threat Map module displays world attacks by indicating the progress of the cyber attack on the world map, categorizing it, and geolocating the event path from source target to destination.
HB
hack back
It is the core module of TssT, it allows you to actively defend the infrastructure by counterattacking the targets detected as attackers.
The module consists of several phases:
- Information Gathering: detects sensitive information of the target.
- Active Attack: Attacks the target with Cross Site Scripting, Sql Injection and Path Traversal attacks.
- Deep Attack: Attack the target by performing a Ddos.
- Send APT: Sends a Keylogger payload to the attacked target via the e-mail carrier.
SB
SANDBOX
It allows you to run Malware Analysis in two ways:
- in a hybrid version using the hybrid sandbox,
- in Manual mode, making use of the analysis of the intelligence team, which will draw up the analysis report with the detection of the impacts and any exfiltrated data.
RD
ROUGE DEVICE
It is the module for intercepting anomalous devices in the protected infrastructure. Through a monitoring script it detects and analyzes the rouge device, putting it in the black list.
In addition, it alarms the control structures, and blocks the device on the perimeter firewalls and on the IPS probes of the protected infrastructure.
RI
REMOTE INSTALLATION
It is able to remotely install the TssT agent, directly from the agent dashboard repository, without manual intervention.
VS
VULNERABILITY SCANNER
The module uses the Openvas open source framework to scan targets for known vulnerabilities.
PM
PERFORMANCE MONITOR
The module makes use of the open source Zabbix framework, to detect the performance of the type of band used in the network, or by individual clients.
TT
TROUBLE TICKET (TT)
Allows you to open a support TT directly from the dashboard, the TT will be automatically taken over by the Tecninf specialized assistance technicians.
